This downloader is also the payload - (Πατήστε δεξιά για μετάφραση)
Researchers at Microsoft have spotted a Trojan downloader that does
something very savvy yet rare: It deletes its own components so
researchers and forensics investigators can't analyze or identify it.
The so-called Win32/Nemim.gen!A
Trojan is also unusual in that unlike most Trojan downloaders that are
put in place to deliver the real payload, this Trojan is also the
payload, according to Jonathan San Jose, a member of Microsoft's Malware
Protection Center.
But the researchers lucked out and found some pieces of the malware.
"Most URLs that this trojan attempts to connect to for downloading are
currently unavailable, but we got lucky and were able to find some of
its components to investigate further," San Jose wrote in a blog post.
Nemim.gen's ability to delete its components can wreak havoc for
forensics investigators and malware hunters. "This prevents the files
from being isolated and analysed. Thus, during analysis of the
downloader, we may not easily find any downloaded component files on the
system; even when using file recovery tools, we may see somewhat
suspicious deleted file names but we may be unable to recover the
correct content of the file," San Jose said.
Malware increasingly is becoming mores sophisticated, and the more
advanced attackers are employing techniques to fly under the radar.
[Zero-day and rapidly morphing malware is proliferating across the Web. Is your enterprise ready to stop it? See Malware: The Next Generation.]
Jaime Blasco, labs manager at Alien Vault Labs, says he's seeing more
malware with built-in anti-forensics features as well as the ability to
deter investigators.
"In the case of Nemin, it is a clever idea since the analysts won't be
able to determine the origin of the infection, and the infrastructure
used to infect the systems will remain undiscovered for a longer
period," he says. "In addition, most of the security companies rely on
automatic environments that execute and emulate malicious programs. We
have seen how more and more malware families are beginning to add
capabilities to detect these environments and deter emulation. We have
also seen some malware samples that only get activated if they detect
human clicking activity on the system."
Microsoft found two components of the Trojan that it downloads and runs,
including a file infector and a password-stealer. The file infector --
which Microsoft identified as Virus:Win32/Nemim.gen!A -- tries to infect
executable files in removable drives. The password-stealer --
PWS:Win32/Nemim.A -- targets user credentials in email accounts, Windows
Messenger/Live Messenger, Gmail Notifier, Google Desktop, and Google
Talk.
The Trojan sometimes appears as part of a display graphics driver in
order to camouflage itself, typically as a file called igfxext.exe,
according to Microsoft.
"If you're infected with TrojanDownloader:Win32/Nemim.gen!A, we
recommend you change all account passwords after you've cleaned your
system, as it's likely you've also encountered PWS:Win32/Nemim.A," the
password-stealer, San Jose said.
ΠΗΓΗ
Dark Reading
By Kelly Jackson Higgins
http://www.darkreading.com/
April 8, 2013
Russian anti-virus company Doctor Web has gained control over a botnet created with BackDoor.Bulknet.739 that, on average, is infecting as many as 100 computers per hour. The Trojan facilitates the sending of massive volumes of spam from infected computers. BackDoor.Bulknet.739 mainly targets machines located in Italy, France, Turkey, the USA, Mexico and Thailand.
The first time BackDoor.Bulknet.739 drew the interest of Doctor Web's analysts was in October 2012. They discovered that the Trojan was being used to connect computers into botnets and was enabling criminals to carry out mass spam mailings.
When the malicious code is executed in a compromised system, a Trojan downloader is extracted, after which another program, detected by Dr.Web as BackDoor.Bulknet.739, downloadsBackDoor.Bulknet.847. The program uses its hardcoded encrypted list of domain names to pick an address to download the spam module. In response, the Trojan obtains the site's main web page and parses the HTML code in search for the image tag. The encrypted code of the mainBackDoor.Bulknet.739 module is stored inside the image tag pair. The module is designed to send huge volumes of unsolicited e-mails.
BackDoor.Bulknet.739 receives from a remote server addresses to which it can send spam, an e-mail template file and a configuration file.BackDoor.Bulknet.739 utilizes a binary protocol to communicate with criminals. It can be directed to carry out updates, download new message templates and spam address lists, or stop sending messages. If the Trojan process terminates abnormally, it can generate a report and send it to the intruders.
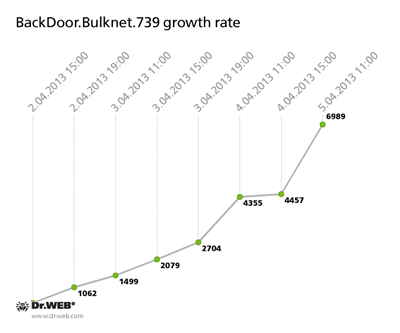
Doctor Web's analysts managed to hijack a server used to control theBackDoor.Bulknet.739 botnet and gathered statistics. As of April 5, 2013, over 7,000 bots were connected to the server. The graph below illustrates how the number increased in the period from April 2 to 5:
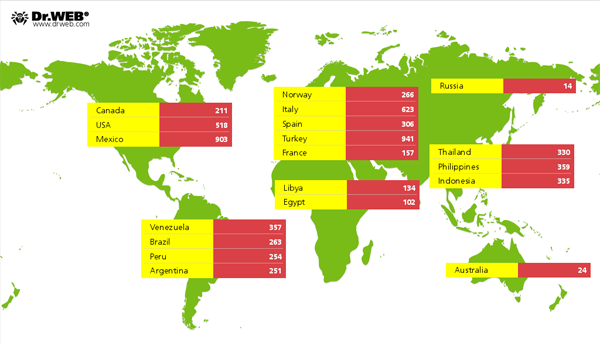
At the moment, the botnet BackDoor.Bulknet.739 is continuing to grow quite rapidly—an average of 100 machines are being infected every hour. The Trojan is spreading most widely in Italy, France, Turkey, the USA, Mexico and Thailand. The smallest number of compromised hosts is found in Russia and Australia. Here's how the infection is spreading across countries and continents:
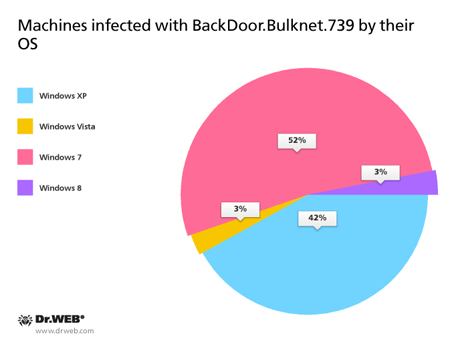
And here are the statistics regarding the operating systems of infected computers:
Doctor Web analysts are continuing to monitor the situation closely.BackDoor.Bulknet.739 poses no threat to systems protected with Dr.Web software since the malware's signature is present in the anti-virus's databases.